Gain Access to the System-Testing 1/2{Ethical Hacking}
I really enjoyed hanging out in this lab. I worked on Kali Linux and windows using many different tools. I intrusioned my host and virtual machine in different ways, using fatrat and Metasploit. Most examples shown in the lab will not pass anti-virus programs and firewalls in real life. So I created exploits embedded in extensions like pdf, jpeg, and Docx. I created more hidden and powerful exploits. I have more than 100 screenshots in total. Of course, I will only share lab tasks and prevent the file from turning into an hackencyclopedia. : ) I hacked even into my own android phone. :)
Responder: I first encountered the responder tool while reading the hacker playbook. It's a simple to use tool that gives good results.
Even if I easily reached my NTLM hash, I could not crack the password because my password was ultra-difficult.
L0phtCrack: I saw the name of this tool for the first time in a book. It was featured in the stories in the book "The art of intrusion" by Kevin D. Mitnick, who is my favorite hacker. The story of the people who developed this tool was awe-inspiring. That's why I have used the tool more than once. Although it was more popular in the early 2000s, it is a must-have tool in the toolbox.
Armitage: Armitage is a GUI for Metasploit. It provides easy use for infiltration or pen-testing to the host. But some bugs occur in the new update Kali Linux. It causes difficulties, especially in creating attacks. It would be best to choose exploits as the poor, but even that doesn't stop the process freeze.
As we know, I first scanned the network with Nmap; then, I set my target. I scanned by right-clicking on it. Then I made the exploit settings. And I activated the attacks. By right-clicking on the target, we can select the attacks and start the attack. The rest are the ways we know.
Now I try to hijacking the machine using metasploit. Of course, first, I did a Nmap scan of the virtual machine I installed. As you can see, my virtual machine looks like a party with no admission fees.
Now I logged into Metasploit. I searched for the appropriate exploit for port 5900. And I got the password. Then I entered the system using vnc viewer.
Even by looking for another vulnerability. I exploited it. I logged into the target as a result of the grabbing banner with using telnet and metasploit .
I entered the target machine through all open ports. It was simple, but it was good exercise. Now is the time to enter my main computer with the malware I prepared with
FatRat: I started fatrat in kali Linux and created my malicious file.
I opened the file on a windows machine. In the meantime, I started operations on Metasploit on Kali Machine.
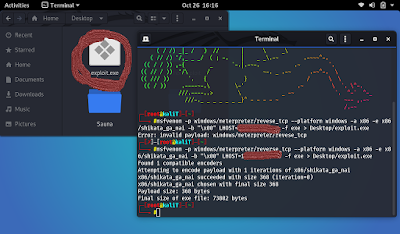
I accessed the machine. Another way will be to gain authorization on the target machine with the malware we create with msfvenom and control it. I created the file, as seen in the visual. Then, after going through similar processes, I gained control of the target machine. I did everything I wanted on the target machine with various commands. I even took a photo of myself from the webcam.
I found the password file on the target machine. I manipulated the modification date of the file. I saw the keys pressed on the keyboard by activating the keyscan on the target machine. And I got a pic from the webcam. I wiped my footprints and shut down the system.
This was my favorite part that made me be the most paranoid. Whenever I sneak into the target machine like this and discover that I can do too much, it pushes me to take more precautions against hackers.
Thanks and Regards
Tarkan Aydınonat





















Yorumlar
Yorum Gönder